During the past year, ransomware gangs have shifted their focus towards cities and councils.
These attacks have quickly become commonplace. US cities, in particular, have regularly been subjected to ransomware, disrupting their operations on a massive scale.
Elsewhere, an attack on Redcar council in North Yorkshire affected 135,000 people and reminded the UK as to how devastating ransomware attacks on city service providers can be.
Restoring services after ransomware attacks is always financially and reputationally expensive because of the cost of downtime during recovery, calculated to be about $10,000 per day. This is the case even when restoring backup systems or decrypting following payment of the ransom, because flaws in the malware often mean that data is not always returned in its previous state and requires further work. The City of Baltimore estimated that its 2019 attack cost $18.2 million.
Cities under siege
Our research on ransomware attacks against organisations has found that their scale and intensity escalated since the last quarter of 2018. In addition, there has been a dramatic increase in attacks on entities that provide services to or manage organisations, like cities. These entities are known as multiple service deliverers.
The following graph shows the rise in the number of attacks against multiple service deliverers, like cities, as compared with single service deliverers, such as a specific department or business.
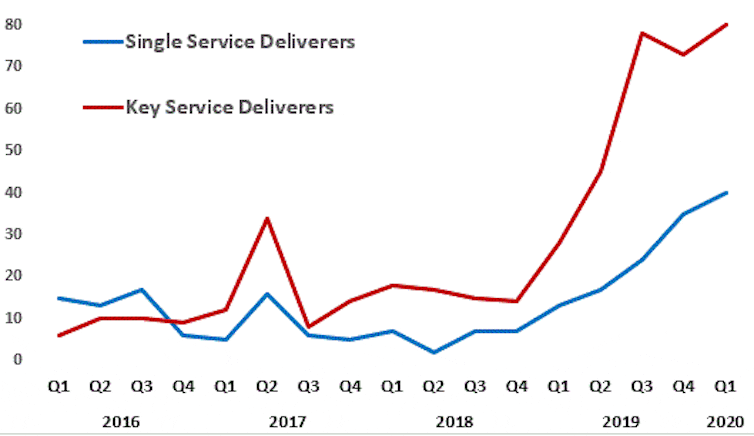
This raises important questions about how cities and municipalities and the services provided by them can fight back against hackers.
My colleague, Lena Connolly, and I found that organisations need to continually improve their security game and be as adaptive as the criminals when responding to attacks. We developed a classification of response tools that organisations must implement in order to respond to crypto-ransomware effectively. We then identified key groups of employees such as front-line managers and senior management who must take an active role in ensuring the organisation is prepared for cyber-attacks.
Practical approaches to defence against ransomware can be taken. These include regularly keeping different formats of backup data in different places, alongside a data restoration plan, and having good ransomware malware protection in place.
Cities should also encourage good cybersecurity hygiene practices by staff. This includes training against social engineering attacks like phishing, which rely on psychological manipulation. We found cybersecurity measures often focused on technical issues and neglected these social aspects.
Fighting back
Other, less formulaic ways of fighting back against ransomware are also being adopted. One option is taking legal action against ransomware facilitators.
In a recent development, the MAZE group and other ransomware groups have begun carrying out attacks by stealing data, then encrypting the computer system and naming and shaming victims on their public websites. The groups then threaten to publish data on the website if payment deadlines are not met. The City of Pensacola in Florida, for example, was hit by a MAZE ransomware attack and a ransom demand of $1 million in December 2019. Some of their data was later released after non-payment.

The response of US company Southwire provides an example for cities facing these attacks. Southwire was a victim of MAZE ransomware and was named on the group’s website. The company took out a US civil injunction against the hosting web provider in the Irish Republic which named the hoster (and shamed them). This led to the offending website being taken down, although it reappeared a few days later on a different web host – which, at the time of writing, no longer appears to be accessible. The action bought some breathing space and also sent a symbolic message to web hosters to act responsibly.
Other positive news is that cybersecurity research is using artificial intelligence to identify and mitigate ransomware attacks as they happen. Darktrace, for example, is one of a number of firms using AI against ransomware.
On the other hand, obstacles to fighting ransomware remain that need to be resolved quickly. In the US, there is confusion over funding measures against ransomware as it falls between federal and state authorities.
In the UK, the problem of reporting serious ransomware attacks is exacerbated because they are in effect two separate crimes, the “ransom” which is an economic crime and the “ware” (malicious software) which is a computer misuse crime. They therefore fall under the responsibilities of different policing agencies.
Prevention is the main order of the day. A number of cities and organisations have so far managed to remain safe or mitigate the impact of attacks. These cases appear to have had robust business continuity plans which combined tried and tested social and technical measures.

