The Conversation, along with many other sites, was rendered unavailable for several hours today after one of its service providers was subjected to a massive “denial of service” attack timed to coincide with “Cyber Monday” in the US.
The attack, emanating mostly from China, targeted a Domain Name Service provider DNSimple and has lasted several hours. DNSimple provides services that translate a name like www.uwa.edu.au into an Internet address 130.95.128.140.
Denial of service attacks are ones were very large volume attacks called “DNS Amplification Attacks”. These attacks bombard servers with so many requests that the servers stop being able to respond normally to legitimate requests. They are called amplification attacks because the attackers use badly configured services that can be found all around the Internet to join in the attack and make it much worse.

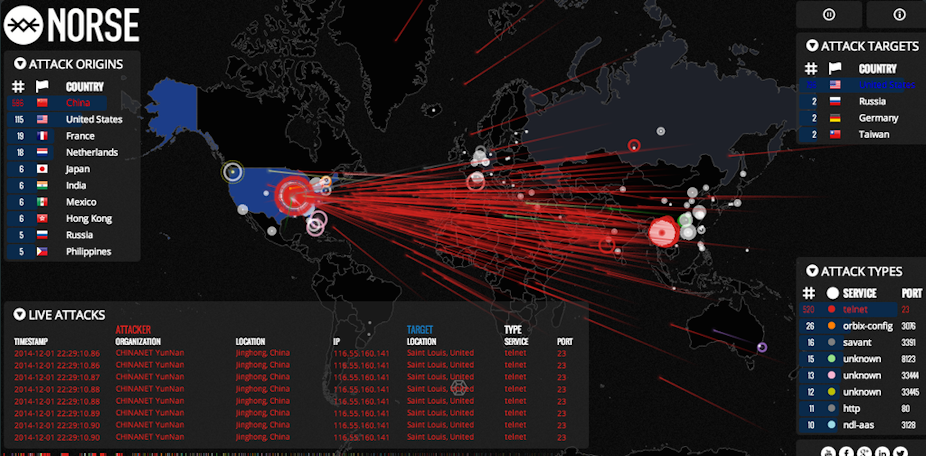
Real time visualisations of cyber attacks on sites like Norse illustrate very clearly the ongoing wars that are continuously playing out on the Internet with most of the attacks originating from China although the United States comes a close second. The attacks that originate in the US and China may actually be infected machines, including PCs and mobile phones that are remotely controlled to join in attacks started elsewhere.
Who exactly is behind the attacks is also unknown. It could easily be independent hackers or governments and the military of those governments with China’s People’s Liberation Army’s Third Department being a favourite service to blame.
The Conversation was not the only site affected. Hundreds of sites were down with site owners resorting to Twitter to inform their users and to vent their frustration.

Preventing these types of attacks is very hard and so Internet providers use a range of strategies to protect themselves against them. One is to spread their services geographically so that if one service gets targeted, they have capacity elsewhere. This is also a strategy that customers of these services can, and should, adopt. Instead of relying solely on one service, websites can use a second service that they can switch to in case of an attack on the first.
Internet providers can also use other means to try and filter out attacks of certain types and finally they can just increase the capacity of their machines and Internet connections to diminish the effectiveness of the attacks.
The attacks however do illustrate a fundamental weakness of the Internet with tens of thousands of misconfigured and infected machines making the entire network vulnerable to these types of attacks. Unless there is a concerted effort to clean up these machines, or to take them off the Internet, these types of attacks will continue.
In this attack, it seems DNSimple were simply overwhelmed with the scale and nature of the attack rather than it being any inherent fault in their services. Unfortunately this will not bring much comfort to the website owners still waiting for their services to return to normal.