Published:
In January 2020, Debi Gamber studied a computer screen filled with information on scores of check deposits. As a manager for eight years at a TD Bank branch in the Baltimore suburb of Essex, she had reviewed a flurry of account activity as a security measure. These transactions, though, from the ATM of a tiny TD branch nestled in a nearby mall, struck her as suspicious.
Time and again, Gamber saw that these checks were payable to churches – many states away from the Silver Spring shopping center branch – yet had been deposited into personal accounts, a potential sign of theft.
Digging deeper, she determined that the same customer service representative, Diape Seck, opened at least seven of the accounts, which had received more than 200 church check deposits. Even fishier, the purported account holders used Romanian passports and drivers’ licenses to prove their identities. Commercial bankers rarely see those forms of ID. So why were all these Romanians streaming into a small branch located above a Marshall’s clothing store?
Suspecting crimes, Gamber submitted an electronic fraud intake form, then contacted TD’s security department to inform them directly of what she had unearthed. Soon, the bank discovered that Seck relied on Romanian documents not just for seven accounts but for 412 of them. The bank phoned local police and federal law enforcement to report that an insider appeared to be helping criminals cheat churches and TD.

The news delighted federal authorities: Since August 2018, they had been investigating a rash of thefts from church mailboxes around the country, and now they knew the bank accounts used by some of the crooks. Determining who these people were took weeks – Seck opened the accounts using false identities. But by April, agents had the name of at least one suspect and surveilled him as he looted a church mailbox. The next month, TD told law enforcement that they discovered another insider – this time at a Hollywood, Florida branch – who had helped some of the same people open bogus accounts there.
Nine months after TD’s tip, agents started rounding up conspirators, eventually arresting nine of them for crimes that netted more than $1.7 million in stolen checks. They all pleaded guilty to financial crimes except for Seck, who was convicted in February for bank fraud, accepting a bribe and other crimes. He was sentenced in June 2023 to three years in prison.
How could it happen? How could criminals engineer a year-long, multi-million dollar fraud just by relying on a couple of employees at two small bank branches in a scheme with victims piling up into hundreds?
The answer is because it’s easy. Crimes like these happen every day across the country. Scams facilitated by deceiving financial institutions – from international conglomerates to regional chains, community banks, and credit unions – are robbing millions of people and institutions out of billions and billions of dollars. At the heart of this unprecedented crime wave are so-called drop accounts – also known as “mule accounts”– created by street gangs, hackers and even rings of friends. These fraudsters are leveraging technology to obtain fake or stolen information to create the drop accounts, which are then used as the place to first “drop” and then launder purloined funds. In the process, criminals are breathing new life into one of history’s oldest financial crimes: check fraud.
To better understand the growing phenomenon of drop accounts and their role in far-reaching crime, the Evidence-Based Cybersecurity Research Group at Georgia State University joined with The Conversation in a four-month investigation of this financial underworld. The inquiry involved extensive surveillance of criminals’ interactions on the dark web and secretive messaging apps that have become hives of illegal activity. The investigation also examined video and audio tapes of the gangs, court documents, confidential government records, affidavits and transcripts of government wiretaps. The reporting shows:
- The technological skills of street gangs and other criminal groups are exceptionally sophisticated, allowing them to loot billions from individuals, businesses, municipalities, states and the federal government.
- Robberies of postal workers have escalated sharply as fraudsters steal public mailbox keys in the first step of a chain of crimes that ends with drop accounts being loaded with millions in stolen funds.
- A robust, anonymous online marketplace provides everything an aspiring criminal needs to commit drop account fraud, including video tutorials and handbooks that describe tactics for each bank. The dark web and encrypted chat services have become one-stop shops for cybercriminals to buy, sell and share stolen data and hacking tools.
- The federal government and banks know the scope and impact of the crime but have so far failed to take meaningful action.
“What we are seeing is that the fraudsters are collaborating, and they are using the latest tech,” said Michael Diamond, general manager of digital banking at Mitek Systems, a San Diego-based developer of digital identity verification and counterfeit check detection systems. “Those two things combined are what are driving the fraud numbers way, way up.”
Boom years for check fraud
Bank reports of cases of check fraud for both business and personal accounts have more than tripled in the past five years.

The growth is staggering. Financial institutions reported more than 680,000 suspected check frauds in 2022, nearly double the 350,000 such reports the prior year, according to the Treasury Department’s Financial Crimes Enforcement Network, also known as FinCEN. Through internet transactions alone, swindles typically facilitated by drop accounts cost individuals and businesses almost $4.8 billion last year, a jump of about 60% from comparable fraud losses of more than $3 billion in 2020, the Federal Bureau of Investigation reported.
Plus, a portion of the estimated $64 billion stolen from just one COVID-19 relief fund went to gangsters who rely on drop accounts, according to a Congressional report and an analysis from the University of Texas at Austin. Criminals using drop accounts also hit the pandemic unemployment relief funds, which experienced improper payments of as much as $163 billion, the Labor Department found. Indeed, experts say the large sums of government money meant to combat economic troubles from COVID-19 fueled the rapid growth of drop account fraud, as trillions of dollars in rescue funds were disbursed in the form of wires and paper checks.
“There were a huge range of criminals who were trained in this during the pandemic,” said one banking industry official who spoke on condition of anonymity because of the sensitivity of the matter. “A lot of them have grown up in the pandemic and seen that it is easy to make a lot of money with these schemes, with very little risk of prosecution.”
In the end, the financial world is witnessing a chaotic transformation of the fraud ecosystem of lawbreakers, victims and governments. The triangle of increased criminal sophistication, weak enforcement and an abundance of personal and business identities literally waiting to be snagged off the streets has fueled this cycle of larceny, one that shows no sign of slowing.
The cycle of fraud
On a warm October afternoon in Orlando, Florida, a lanky young man crouched in the parking lot of Grace Alive Church, watching a mail carrier approach his truck. The postal employee glanced at the man, noticing his red plaid pajama pants, black hoodie and white surgical mask. The carrier opened the truck door and started grabbing mail to drop off at residences on Balboa Drive.

The man in the hoodie suddenly appeared beside the mail carrier, who noticed a handgun stuffed in the young man’s waistband. “Give me your arrow key,” he said, according to court records.
An arrow key. The U.S. Postal Service’s universal key that opens blue public mailboxes, parcel lockers and apartment panels. The mail carrier struggled with the key chain attached to his belt as he attempted to appease the man robbing him.
“Hurry up,” the robber said. “There are kids around. I don’t want to hurt any kids.”
Finally, the carrier successfully removed his truck key and handed over the chain with the arrow key. The robber walked across Nowell Street and hopped into a waiting Jeep Grand Cherokee, which immediately took off.
Until recently, muggings of letter carriers were relatively rare, but they have grown in tandem with the explosion of drop account frauds. Stealing the key is often the first step in a cycle of crime that ends with banks and individuals scammed out of hundreds of millions of dollars.
These types of robberies only occurred 80 times in 2018, but now are almost a daily event. In fiscal 2022 and the first half of fiscal 2023, letter carriers were robbed 717 times, Postal Service statistics show. In 95% of those cases, the criminals only wanted the arrow key, according to Frank Albergo, president of the Postal Police Officers Association. “It’s completely out of control,” he said.
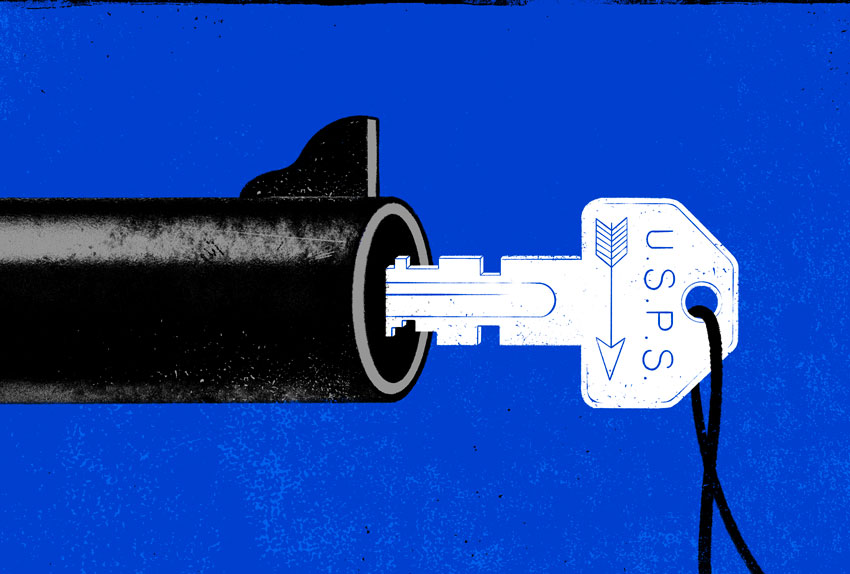


With street gangs, the cycle of crime usually follows the same pattern. First comes the theft of the arrow key.
That is then turned over to another gang member, who uses the key to open public mailboxes and steal the contents. Those thefts can go on for days; one key opens as many as 600 boxes.
The mail thief then dumps the mail in the car and drives it to the gang members responsible for sorting. The piles of paper are separated, removing every check, credit card or other financial instrument as well as any document that can be used to steal an identity. Everything else is thrown away.
To open the drop accounts, others prepare IDs using the personal identity information stolen from the mail, hacked online, or purchased from a seller online.
After six years of largely ignoring the issue, the Postal Service announced on May 12 that it would replace arrow keys with electronic locks. But the news is far less cheery than it seems. While its engineering staff has been exploring possibilities, the Postal Service’s contracting process that would be necessary for the final design and manufacture of locks entails 264 steps and requires years from start to finish; it has yet to even start with the first major step of issuing a request for proposals. Plus, it only plans to first release them in a handful of cities. In other words, thieves have a very, very long time to keep stealing arrow keys.
Louis DeJoy, the postmaster general, acknowledged in Congressional testimony on May 15 that, despite the announcement, electronic locks would not be in place anytime soon. “This is a several year project,” he said.
How are the keys central to the drop account frauds? Once stolen by a gang member, the key is passed to another gang member who uses it to loot collection boxes and apartment panels. The thief then drives the stolen mail to gang members responsible for sorting. That group then separates every check, credit card or other financial and identity information.
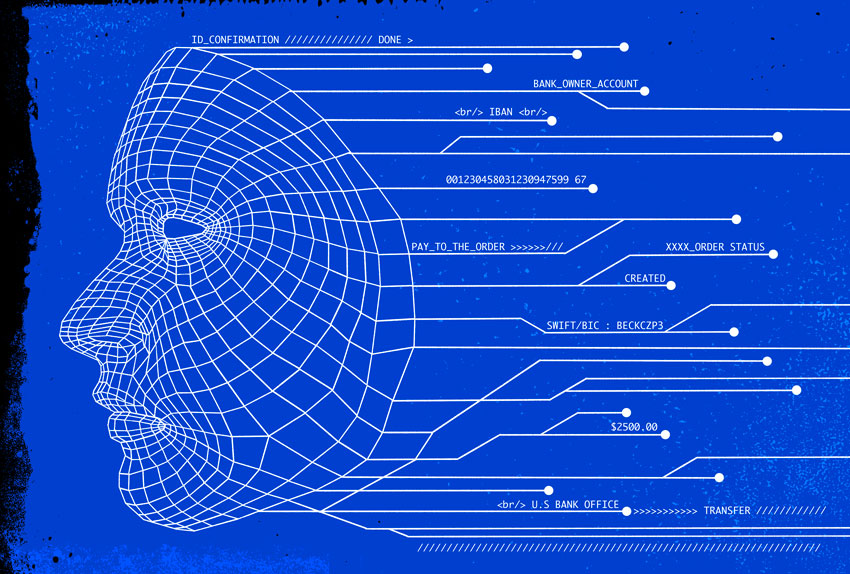
Personal data found in stolen mail gives the gangs the names and addresses of potential victims. From there, the criminals search online databases – both legal and illegal – to gain access to dates of birth, Social Security numbers and other personal information, potentially including email addresses, driver’s licenses or passport numbers. This provides what in fraudsters’ slang is called fullz (pronounced fools), which stands for “full credentials.” It’s also the name used by the gangs for the person running online criminal marketplaces.
The fraudsters sometimes access secure systems at credit rating agencies that maintain financial and identifying information for millions of people. For example, our investigation spotted a video posted to an encrypted fraud channel on Telegram Messenger of someone signing in to what appears to be the TLOxp database, run by the credit rating agency TransUnion. That subscription-based system is intended primarily for companies, law enforcement, universities and other official organizations. But the data available on services like TLOxp is even more valuable to fraudsters. By using them, criminals enter a mecca of traditional fullz data plus employment history, unlisted phone numbers, assets, liens, judgments and other data.
The website on the fraudster video appears identical to TLOxp’s Advanced People Search product. In a statement, however, TransUnion suggested that the street gang posting the video instead designed their own website to make it appear as if they had obtained a TLOxp subscription when they had not. The company said the website on the video and the TLOxp site contain “subtle differences” that it would not identify and which are not apparent. Also, the second page shown on the video that TransUnion says was copied is only accessible for review through subscription. The company added that, “data security is TransUnion’s top priority,” and that it scans for references to TLOxp on the internet “to uncover any possible misuse of data.”
Access to this data makes opening drop accounts easy. Fraudsters often access bank websites by cell phone using disposable SIM cards; credentials in hand, the swindlers then establish drop accounts. Sometimes, they make a small deposit with clean money, but often that’s unnecessary: The gangs know which banks will keep an account open for a short period even if it holds no cash. In short order, the criminals receive a debit card delivered to a drop address – such as a rented or purchased house – and in short order, the bogus account is ready for use.
Meanwhile, other gang members have been doctoring the stolen checks. Check washing soaks off written ink by using a blend of acetone and gas-line antifreeze, creating a blank that can be filled out for many thousands of dollars. From there, the check is made payable to the name on the drop account, deposited, and the cash is removed at an ATM. There’s also a tactic called “check cooking,” where criminals scan the check and copy the signature using photo editing software. Then, they use that same software to add victim and banking information onto a stock check, and apply the signature, creating a forgery ready to be filled out for any sum.

Larger withdrawals sometimes require in-person bank visits, which brings more conspirators into the scam. Offering $200 to $300, so-called brokers recruit elderly or disabled people in hopes that bank tellers will be less likely to question their credibility. If needed, brokers give their hires new clothes and haircuts, then take them to the bank.
There, these “walkers” bring debit cards for drop accounts and fake IDs. Since there is nothing about them to indicate they are not an established customer, tellers cash checks based on the existing balance of stolen money in the drop accounts.
Often, walkers wear devices like AirPods connected to their phones, allowing the driver outside to provide real-time instructions in handling the withdrawal. According to an industry official who spoke on condition of anonymity because of the sensitivity of the issue, banks have begun instructing branch employees to keep an eye out for people wearing earpieces, but tellers are not trained to stop sophisticated organized crime.

The marketplace
On one of the dozens of Telegram fraud channels we monitored, users griped about prices. A single washed check, or slip, was too expensive at $250, they grumbled. Annoyed, a gang member posted an audio response to put the customers, known as carders, in their place.
“Ya’ll in the game where you’re spending $250, and you’re making $30, $40, $50,000, and you n*****s complainin’, complainin’ about prices,” he said in the recording. “Every fullz in the game should be chargin’ ya’ll at least $1,000 for each slip that we sell. We’re in a thousand-dollar business. We ain’t in no $100 business, bro. So, stop (complaining).”
Moreover, he said, gang members were the ones risking prison. “We take all the risk for ya’ll to do what ya’ll will do. Ya’ll won’t even go to jail (unintelligible) cookin’ the slip up and dropping that sh*t in people account. …We can’t tell these crackers that we sold a slip to such and such and such for $250, so therefore you get 10 years. That’s not how that works, man. Pay the n****r that’s helping you eat!”
Needless to say, the carders’ attempt at price negotiation failed.
So it goes in the fraud marketplaces on Telegram, whose freewheeling channels are increasingly used by street gangs to peddle their wares and provide tips and techniques for committing bank fraud.
The Telegram channels often show photographs and videos of credit and debit cards for drop accounts obtained through stolen or fictitious identities. They also display other available goods, including details of existing drop accounts, ATM receipts showing the amount already deposited, stolen and counterfeit checks, tax refund checks, arrow keys and more. There are slick advertisements, complete with music and visual effects, for video tutorials priced around $500 that provide step-by-step instructions on how to open the accounts. And to entice skeptics, images often display piles of cash.
Prices vary based on the qualities of stolen or fake identities. Long-standing identities with good credit scores are worth more than freshly purloined ones. One Telegram fraud marketplace offered a nine-year-old identity with a perfect payment history, three open payment cards at three banks, and a credit score of 800. The price: $2,500.

The criminals also sell fake Social Security and ID cards that can be used by walkers at the banks. Videos on the platform demonstrate how the gangs can rapidly create sophisticated IDs – one fraud channel shows black lights illuminating otherwise invisible holograms on driver’s licenses, a security feature used by Transportation Security Administration screeners at airports to confirm an ID is real.
Deepfake software that creates talking, moving fictional people is also available. Now, live streams using newly sophisticated deepfakes help in “romance scams”, where fraudsters target lonely people to gain their affection; once victims are fooled into believing they have found romance online, the scammers convince them that they need money for some emergency. If the target agrees, the fraudster provides wiring instructions, often to a drop account.
The criminals also market on their Telegram channels through rap videos. The lyrics sometimes provide explanations of how the crimes are done and show piles of cash. One rap video we found is about debit card fraud. Called “Swipe It Up,” it provides details on committing the crime, including reminding listeners to confirm transactions when banks text their burner phones asking about possible fraudulent charges. Some of the lyrics are:

Swipe it up and get it goin’.
I mean a lot.
I got a customer on the phone.
And if you get a text
You better not press no.
Swipe it up and get it goin’…
…Add it to the phone.
All I needed is a code.
While street gangs and individual thieves have been primary drivers of drop account frauds since 2020, traditional hackers also remain big players. They sell the same information available on Telegram channels but use the dark web to do business.
Hackers don’t rob letter carriers, but rely on online theft of fullz data. A common technique is known as “digital skimming,” in which hackers access payment card information entered on checkout pages of online stores. But the easiest way for hackers to get their hands on fullz is to shop at one of two types of dark web marketplaces. The first is called “underground hacking websites,” which are used by sophisticated criminals who already stole online data and want more.
“Underground hacking website is where you can trade or sell or buy hacking, or you can talk to any other hackers,” said Hieu Minh Ngo, now a cybersecurity consultant in Vietnam who formerly ran a fraud market website until his 2013 arrest in the United States. “And then you can see lots of stuff, illegal stuff, like ATM card, stolen credit card, Social Security number, date of birth, driver’s license, fullz information.”
The second hacker marketplace is called carding forums, which operate more like Telegram fraud channels. They attract customers with limited or no hacking skills but who know how to commit banking and credit card fraud. One of the biggest such forums is Bidencash, which opened in March 2022. After starting with a low profile, its operators last June announced they had 7.9 million payment cards for sale. At its one-year anniversary, Bidencash celebrated by releasing 2.2 million more debit and credit cards.


While different groups of criminals patronize different marketplaces – Telegram channels for street gangs, dark web forums and sites for hackers – the tactics facilitated by those marketplaces have begun to converge inadvertently, as crimes by one group feed the fraud of another.
In 2017, for example, hackers attacked Equifax, the credit rating agency, stealing identity information of about 147 million people. That data soon appeared on hacking marketplaces. Class action lawsuits followed; Equifax established a settlement fund, which did not return emails seeking comment; people who lost up to $20,000 could file claims. Then, in an inexplicable blunder, the Equifax fund paid settlements with checks sent by mail, where street gangs could steal them. And steal they did.
Checks to settle damages caused by the Equifax hackers are now available for purchase on street gangs’ Telegram fraud channels, ready for deposit into drop accounts.

The crimes
In the spring of 2021, thousands of messages with the word “Womply” flooded Telegram fraud channels.
“Been hitting Womply,” one read. “Don’t sleep on it.” Another user messaged, “GET PAID WITH WOMPLY SAUCE EASY $10K-$20K.” Meanwhile, in Orlando, law enforcement officials conducting a drug trafficking investigation listened on wiretaps to members of the Orange County crime organization Army Gang as they raved about Womply:
You ain’t got nobody who want run their s■■t on Womply?
What the f■■k is Womply?
Man, that’s the website that, that really hittin’.
I don’t know what the f■■k that is.
Neither did the law enforcement officers monitoring the conversation.
Womply is one of about 20 financial technology firms paid to administer the Paycheck Protection Program, the loan program to help businesses meet payrolls during the COVID-19 pandemic. Its role was to process applications for loans, screen for fraud, and directly distribute or authorize payments from the Small Business Administration through financial institutions.
Problem was, as street gangs quickly figured out, Womply could not handle the job, setting off the flurry of chatter about the company. Founded by a convicted felon, it never conducted high-volume loan processing or large scale financial crime compliance. Its system, as an executive from a financial firm that issued Womply-approved loans told Congressional investigators, was “kind of put together with duct tape and gum.” Womply did not respond to a request for comment.
The gangs flooded Womply with bogus applications for nonexistent companies, providing forged tax documents as proof of qualification for loans. Advertisements for new products that tricked Womply’s security appeared on fraud channels. To bypass facial recognition, they sold computer-generated 3D heads, posting videos that showed the Womply system could not distinguish them from real faces.
Within days of the Telegram wave of messages, Benworth Capital, a Womply partner that handled approved applications, warned the company that it might have to shut down. “We are managing our banking relationship very closely because they are anxious with the amount of fraud they are seeing,” Bernie Navarro, Benworth’s president, said in a May 7, 2021, email to Womply. “Bluntly stated, we have been on the brink of being closed 3 times.”
The online attack on Womply shows the scope of the frauds facilitated by criminals’ use of drop accounts. Check-washing and stealing identities brought in big profits, but the fraudsters also go after big money from businesses and governments.
One of the most lucrative of the schemes to cheat the government is called tax refund fraud. With that scam, criminals use identification information of small businesses or individuals to claim refunds by filing bogus tax returns. Since refunds are sent without a prior audit, the IRS either mails a check or wires the money into a drop account.

Individuals are the easiest targets. Using fullz, the fraudsters have enough data to file fake returns to the IRS in the name of the victim and then send the cash to a sham account using that same personal information. Small businesses can be more lucrative targets; the criminals only need the employer identification number of a real business to send in a return. Even simpler, the fraudster steals or buys a Social Security number, uses it to obtain an employer number and files a fraudulent return on behalf of a business that doesn’t even exist.
The perpetrators imitate a taxpayer by using information from stolen identities, then apply for copies of previous tax statements. “You go through an identity check, and since you should know everything about this person, its (sic) no problem at all,” a fraudster dubbed anthonyshane wrote about the IRS system in a drop account handbook posted on the dark web. “I have not had any issue retrieving past tax returns. Its (sic) a great tool to use to figure out a person’s income and also tells you if this person is a viable victim.”
The rewards on refund frauds can be astronomical. Seven co-conspirators were indicted in March for using stolen identities to file 371 bogus returns claiming $111 million in refunds, which were deposited to prepaid debit cards and drop accounts. A ring of at least 10 California residents filed about 7,000 bogus tax returns in a plot that ended in 2016, claiming refunds of $38 million; the IRS paid more than $14 million to the criminals in drop accounts at J.P. Morgan Chase, Citibank and other financial institutions. The money was deposited using stolen identities and in the names of fake businesses like Harhak Diamonds and Abraisyan Jewelry.
A recent IRS audit identified more than 587,000 bogus returns filed in the first nine months of 2022 that illegally sought $4.8 billion in refunds; the audit reported that, just from the illegal returns investigators could identify, about $200 million was paid out.
Some schemes using drop accounts to facilitate defrauding businesses do not require detailed identity information to tap into riches. One tactic used by hackers and their customers is business email compromise. Through that crime, fraudsters find the email address for a company executive with authority to pay bills, then send an invoice to that person, pretending to be a vendor or client. If the executive falls for it, the money goes into a drop account. Then fraudsters grab the cash and disappear.
The profits – and penalties – for these types of fraud can be large. In February 2023, two Maryland men were sentenced to a combined 14 years in prison for their role in such a scheme that netted $13 million. The men and their co-conspirators used emails with bogus addresses to pose as the victims’ business partners and vendors, tricking the companies into wiring huge sums of money to drop accounts at Wells Fargo, Bank of America, TD Bank and Delta Community Credit Union.
A TD spokesman said, “To protect our customers and the bank, TD has strong processes in place to identify, investigate and deter potential fraud.”
Wells Fargo declined to comment about the security measures it has in place to prevent the opening of drop accounts like in the BEC scheme, saying that it could undermine efforts to protect customers. A Delta official said the institution faced no claims of liability in the case, and that it adheres to “industry best practices with fraud detection and prevention.” Spokesmen for Bank of America did not return repeated requests for comment.
These crimes do not just involve co-conspirators in the U.S. running money through domestic drop accounts. For example, Aldrin Fomukong, a fraudster in Maryland, led a global business email compromise scheme involving criminals in multiple states and South Africa who stole from American companies. That money was first deposited into drop accounts in the U.S. before being wired to the Czech Republic, Poland, and other countries. Fomukong and a number of his co-conspirators pleaded guilty, with most sentenced to years in prison.

Businesses are not the only prey of criminals running email compromise scams. Using the same tactic, scammers also target organizations that dole out large sums of money without standard corporate controls: political campaigns.
In the 2022 election, the campaign for Republican Senator Jerry Moran of Kansas received emails containing invoices from a criminal posing as SCRP Media, a political strategy and advertising firm. According to a government filing, the campaign wired the money – $345,000 in October and $345,000 in November – to a drop account at Wells Fargo; only $168,000 was stopped from being withdrawn, costing the campaign more than half a million dollars. The same thing happened to the 2022 campaign of Republican Congresswoman Diana Harshbarger, which wired $186,000 to a drop account of a criminal posing as a legitimate vendor.
But the most audacious fraud on a political entity came in June 2020, when criminals brazenly targeted the campaign of Joe Biden. With just an email containing an invoice and wiring instructions, they directed about $65,000 to a Bank of America drop account, snagging money donated to help elect the current president of the United States.
Failure of oversight
114
The number of stolen checks for sale weekly on a compilation of 60 Telegram fraud channels increased from just over 100 in Fall 2020 to several thousand in 2022.
A confidential 2022 memo from the Postal Inspection Service to the Justice Department issued a dire warning: Armed robberies of mail carriers were growing like never before, with criminals stealing arrow keys.
“At the current trajectory, it is estimated there will be more than 450 armed robberies of USPS letter carriers over the course of 12 months,” read the advisory, which was obtained during our investigation. “This is a substantial upsurge of 400% since 2019.”
The postal inspectors knew why robbers wanted the keys, according to the previously undisclosed memo: Using the arrow keys to break into public mailboxes, criminals gained access to checks, payment cards and personal information that allowed them to steal identities, facilitating mail fraud, wire fraud and bank fraud through drop accounts.

“With the dark web and organized crime promoting these unlawful activities, robberies and mail theft are becoming increasingly more attractive to criminals,” the memo reads. The thefts “have an impact on all citizens and financial institutions whose mail is stolen and used for illegal activities.”
But when the postal service discussed the crisis with Congress six months later, it told a decidedly dissimilar story. Robberies of letter carriers as part of identity theft and fraud schemes went unmentioned. Instead, the inspectors focused on who they declared to be the real culprits: postal employees.
“Our Office of Investigations has initiated Operation Secure Arrow, a multifaceted effort to identify and investigate employees involved in the theft and mishandling of arrow keys,” Melinda Perez, an assistant inspector general, testified.
The Postal Service’s long reluctance to tell Congress details about armed robberies for arrow keys and the subsequent crimes described in its 2022 memo underscores its failure to confront the threat, even with its recent announcement about increasing key security. In fact, the Postal Service may have made matters worse by changing the authority of the Postal Police Officers in 2020. In an Aug. 25 memo that year, the Postal Service directed managers to stop using postal officers to protect letter carriers, and instead use that law enforcement organization solely to guard post offices and other properties.
Responsibility for handling robberies fell to postal inspectors, who were already charged with enforcing about 200 other laws, essentially leaving carriers to fend for themselves. While arrow key robberies have escalated, the inspectors ignored the surge in their most recent annual report; they focus instead on interdiction of illegal narcotics and other crimes.
When they do announce the arrest of someone who robbed a letter carrier, the inspectors often have left the responsibility for cracking the case to local law enforcement, according to the National Association of Police Organizations.
In recent testimony before Congress, the Postmaster General stated that the service does not have statutory authority to assign Postal Police to protect letter carriers. That statement, though, runs counter to the modern history and to the service’s own handbooks describing the police group’s responsibilities as including “mobile patrol(s) or escort protection.” In February, an independent arbitrator said that the Postal Police’s authority remains governed by those handbooks. Moreover, even the 2020 memo states that senior managers have the power to assign the police duties beyond postal property; the Postal Service just has chosen not to do so despite the robbery crisis.
The unwillingness to confront the problem shows in the numbers. According to statistics compiled by the National Association of Postal Supervisors and the Office of the Inspector General, mail theft complaints by the public ballooned 1,096% from 2017 through 2021. In the two years since 2020, armed robberies of letter carriers increased 144%.
That surge has not been met with an increased law enforcement response. Postal inspectors dug into less than 1% of the mail theft complaints between fiscal year 2020 and fiscal 2021, despite having sole responsibility for that job. The number of arrests dropped 39% from 2,487 in fiscal 2018 to 1,511 in fiscal 2021.
Meanwhile, the crimes that follow letter carrier robberies have boomed. The number of stolen checks for sale on 60 Telegram marketplaces climbed from 114 checks per week in the fall of 2020 to about 2,000 in 2022. Money drained from bank accounts was the costliest form of fraud, at $1.6 billion, the Federal Trade Commission reported. Credit card scams led the pack in identity theft losses, with new account fraud climbing 13%.
Arrests and convictions drop
Even as mail theft complaints by the public increased ten-fold, the postal service pursues few cases and both arrests and convictions have dropped.

In other words, as the crimes that often start with stolen mail and end with financial wreckage swell, law enforcement’s response has scaled back. Until the Postal Service and prosecutors get more aggressive, bank officials say, the problem is only going to get worse.
“The government wants us to solve all the problems and not give us any help,” the banking industry official said. “To stop it, the Postal Service needs to attack the robberies, and more of the check and identity thieves need to be prosecuted. These people need to feel some punishment, and right now that’s not happening.”
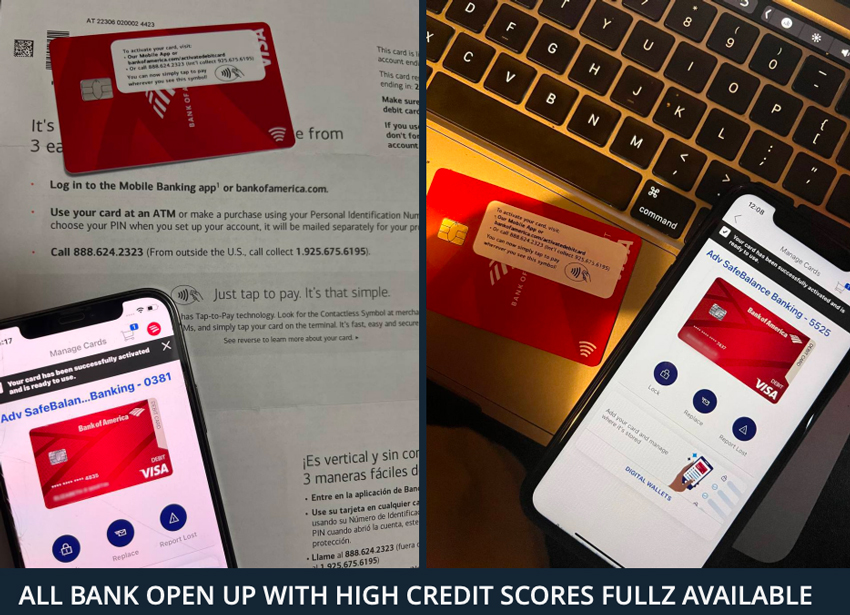
The recklessness of big banks
At 3:27 p.m. on Nov. 28, 2022, Bank of America began processing an account application submitted online by a criminal using a false identity. Two minutes later, the bank asked the imaginary person to confirm his email address. At 4:02, just 35 minutes after it began reviewing the application, the bank emailed the criminal. “Great news!” the email declared – the account was approved and ready for use.
No one from Bank of America ever saw or spoke to their new client before opening the drop account now set to receive illicit funds. No one confirmed that the bank’s new customer was who he claimed to be. No one knew the source of the money that was certain to be deposited soon. And Bank of America wasn’t the only easily snookered bank – less than an hour before it began processing the application for a person bank officials would never meet, Citibank had opened a drop account for the same fraudster.
The roster of banks that have approved stolen and fictitious identities to open these untold thousands of accounts extends far beyond just these two and includes practically every major banking institution in the country, from JPMorgan Chase and Wells Fargo to Capital One and TD Bank, according to court documents and banking industry officials. The American Bankers Association declined comment on the record.
In other words, banks are hardly helpless victims that they contend. Rather, financial experts say, the explosion of drop accounts can only be happening if the banks are largely ignoring some of the strictest regulations governing their operations.
By law, banks are required to support the government’s efforts to combat money laundering and terrorist financing. The pillars of that responsibility are known by a series of acronyms – Know Your Customer (KYC), Know Your Business (KYB), Customer Due Diligence (CDD), and the filing of Suspicious Activity Reports (SARs) – which are Anti-Money Laundering (AML) programs required by the Bank Secrecy Act (BSA).
That mishmash of letters and names is the defense against fraud to flow through the financial system. They can be reduced to a simple concept: Banks need to know who they’re doing business with. That means, before opening an account, banks must gather identifying information of a potential customer, analyze those credentials to confirm they are real, determine if there is evidence of a physical mailing address, and confirm sources of money. For businesses, banks need to check state filings to confirm the companies exist, determine the identities of owners, and collect documents like revenue history to ensure alarms go off if larger deposits than usual suddenly come in.
In the past, applicants sat with a bank official while opening an account, so the process was easy. But the digital age changed that, since customers applying online are now reduced to a series of ones and zeros in computer code, and IDs are only images, not cards that can be held and studied closely. Even obtaining an ink signature, written at the time of application, is impossible. In the past, a new customer had to be prepared with a first deposit to open an account; that is not always required anymore for online accounts.
Customers opened an estimated 13.1 million new bank accounts in 2022 through phone apps and websites, according to a report by Insider Intelligence, a market research company. To win new depositors, banks must make sure the digital application is fast – after all, it is much easier to abandon the process on a phone or a computer than it is to walk away from a bank official helping to fill out paperwork. In fact, according to the Insider Intelligence report, the rate of abandonments of partially finished digital applications surges if the process takes longer than five minutes; with customers using cellphones or other mobile devices to apply, that rate can hit as high as 40%.
That creates a rationale for a competitive race to the bottom: If a bank might lose legitimate customers to other institutions if the application process lasts longer than most pop songs, the pressure to make identification requirements easier is huge. And that, fraud experts say, is leading to an apparent collapse in the banks’ adherence to Know Your Customer and other anti-money laundering rules – a reality fueling the explosion of drop accounts.
“If financial institutions truly knew their customers, none of these drop account problems would exist,” said Dante Tosetti, a former commissioned bank examiner with the Federal Reserve who is now a special adviser to West Coast AML Services, a consulting firm that advises banks on anti-money laundering rules. “If banks slowed these account openings until they could conduct more verification on customers, that would be a very good control. But they don’t do that, because it doesn’t fit their business plan.”
Bank efforts to comply with the anti-money laundering requirements are often little more than meaningless “paper programs,” Himamauli Das, acting director of FinCEN, said in a speech last year. “This often arises when financial institutions put growth before compliance and think about compliance as only a cost center.”
Officials at smaller community banks – where accounts are usually opened in person by nearby residents and local businesses – react almost in disbelief that their mammoth, international brethren with hundreds of billions in assets rushed so quickly into digital banking without preparing for the onslaught of fraud that was certain to follow.
“That these accounts are being opened shows that the banks don’t have robust (anti-money laundering) programs and that the regulators aren’t making sure that they do,” said David G. Schroeder, a senior vice president at the Community Bankers Association of Illinois. “We need to hold the large banks to their responsibility so they stop opening these accounts that are at the heart of this criminal enterprise.”
The community institutions are particularly outraged because they and their customers are victims of large banks’ failure to effectively combat drop account openings. Valid checks written on community accounts are just as likely as any other to be intercepted by gangs robbing mailboxes. Thus begins the journey through the cycle of crime – washed or cooked, rewritten for larger sums, deposited by mobile app into the bogus accounts at large banks, with the cash then withdrawn at an ATM or by a walker. The result is that the customer has been cheated and valid checking accounts at the community banks are illegally drained.
Technically, since the large financial institutions deposited the bogus checks into the illegally opened drop accounts, they bear responsibility for reimbursing the community banks and their customers. But even though the local banks are innocent in all of this, the giant financial conglomerates drag their feet in compensating them. The community bankers’ group in Illinois has taken the lead in fighting big bank intransigence and has begged federal regulators – the Federal Deposit Insurance Corporation, the Comptroller of the Currency, and the Federal Reserve – to intervene.
“The largest banks are enabling a weak link in this crime chain by permitting fraudulent accounts to be opened in the first place,” Schroeder wrote regulators in February.
Schroeder reported grim statistics from a survey of community banks in his letter to regulators. Sixty percent of the small banks in his state experienced problems getting reimbursed from the large institutions responsible for the problem. The community bankers said that, when they do receive reimbursement, it can take as long as 18 months. As for those claims that remain open, in 65% of those cases, the big banks did not even bother to return phone calls from the community banks.
For 2022, the community banks in Illinois experienced losses of $30,000 on average – a small amount for the financial behemoths, but a huge sum that impedes efficient operations at the local institutions. If that average holds at the 4,548 community banks around the country, more than $136 million was drained from these local institutions last year. The regulators responded to Schroeder’s letter – sort of. Despite their traditional standard of refusing to referee intra-industries squabbles, regulators are negotiating a framework to handle the problems at Illinois community banks caused by the failures at the large financial conglomerates. Illinois officials have discussed what they are doing with community bank associations around the country, Schroeder says, in hopes that the others will follow them. But there is a long way to go.
“We’re just in the fourth inning,” Schroeder said. “We are hoping to build some momentum and have an agreement in the next six months or so.”
But with a financial system rife with fraud, six more months of regulatory dithering is an eternity. If the past is any indication, over that time another $65 million will be lost at community banks, millions of pieces of mail will be stolen, untold billions will be defrauded from individuals, businesses and governments, and giant financial institutions will sign off on opening thousands of new drop accounts needed to facilitate the crime.
Meanwhile, street gangs, hackers and organized crime will continue one of the greatest larcenies in American history.