UPDATED 3:20PM AEDT: The NSW Electoral Commission has now publicly commented on the security flaw uncovered by Dr Vanessa Teague and J. Professor Alex Halderman. But as the authors explain below, “we are concerned that the NSW Electoral Commission does not seem to understand the serious implications of this attack”. Read the rest of their response at the end of this article.
If you’re one of the 66,000 people from New South Wales who voted in the state election using iVote between Monday March 16 and midday on Saturday March 21, your vote could have been exposed or changed without you knowing.
How do we know that? Because we uncovered a security flaw in the popular iVote system that would have let us do exactly that, if we’d chosen to. That’s despite repeated assurances from the New South Wales Electoral Commission that:
People’s vote is completely secret. It’s fully encrypted and safeguarded, it can’t be tampered with
As we’ve been able to show, that’s not true.

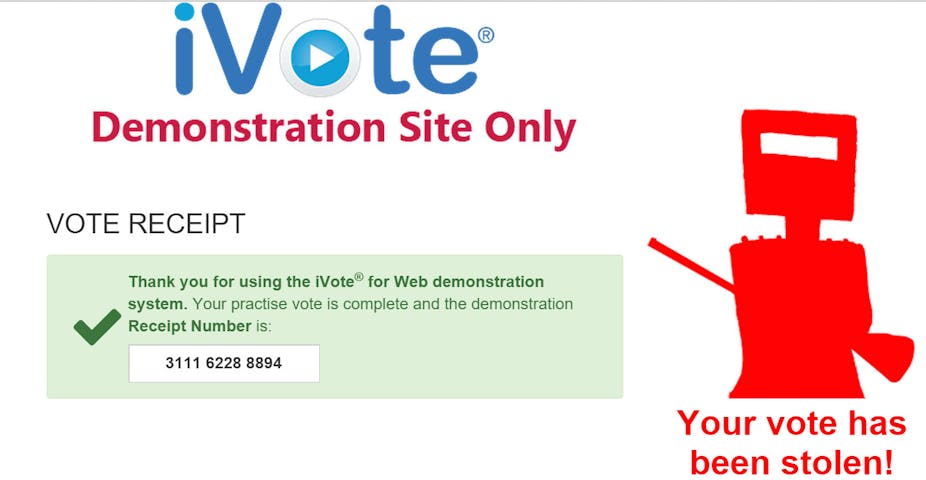
We should stress that rather than do anything illegal or disrupt the March 28 state election result, we tested this security weakness only on our own practice vote at the iVote practice server. After checking that the same weakness affected the real voting server, we alerted the authorities late last week. We also waited until we could see the problem had been fixed before talking publicly about it.
Less than a week to expose iVote’s vulnerability
The problem we found was that the voting server had loaded some code from a third-party site vulnerable to the FREAK attack, a major security flaw that left Apple and Google devices vulnerable to hacking (you can read a recent Washington Post article explaining the FREAK flaw).
How did that global security problem affect iVote? For a longer, more technical explanation of what we did and found, read more here.
The shorter version is that with less than a week of concerted effort, the two of us discovered that the FREAK flaw allowed us – or potentially anyone with the right technical knowledge – to intercept a NSW voter’s internet traffic, and insert different code into vulnerable web browsers. Many, but not all, browsers have been appropriately patched over the last week – this site lets you check whether yours is still vulnerable.
We demonstrated that we could make the voter’s web browser display what the voter wanted, but secretly send a different vote to the iVote voting server.

The iVote system does include a vote verification process for people who choose to vote online or by phone, where they can subsequently call an automated interactive phone line to double-check what vote the system holds for them.
However, that verification system could have errors or security vulnerabilities; we can’t tell you with any certainty either way, since there’s no publicly-available source code or system details.
Given the supposedly “fully encrypted and safeguarded” iVote system proved so vulnerable to attack, we certainly would not recommend people take any chances by voting online in the NSW election.
The NSW online vote is globally significant
The 2015 NSW election is Australia’s biggest-ever test of electronic voting, which has largely been limited to small trials in the past. The official predictions have been that 200,000 to 250,000 people would vote using iVote in this election.
And this NSW election already ranks as one of the world’s biggest online votes to date, on track to exceed the 70,090 Norwegians who voted electronically in 2013, and perhaps even beat the 176,491 people who voted online in the 2015 Estonian election.
In just its first week, even apart from our discovery things haven’t run smoothly.
Early voting using iVote opened at 8am on Monday March 16, and it will close at 6pm on election night, Saturday March 28.
On Tuesday March 17, the NSW Electoral Commission suspended voting for six hours after it turned out that two minor parties had been left off the “above the line” section of the NSW upper house online ballot paper. That problem, blamed on human error, was fixed – but not before 19,000 votes had already been cast.
Serious human errors do sometimes happen in elections, and they can affect paper ballots too.
Our concern about online voting – and specifically about the NSW iVote system – is that security flaws like the one we found last week are still too prevalent and predictable.
NSW vs Washington DC’s approach
Less than a fortnight ago, one of us (Dr Teague) wrote in The Conversation about the potential privacy and vote tampering problems with iVote. That article reflected concerns expressed in a letter to the NSW Electoral Commission in 2013. Yet the commission has never responded meaningfully to those concerns, and also chose not to publicly comment on the FREAK security flaw that we exposed.
However, that’s not the approach taken by electoral authorities elsewhere wanting to deliver trustworthy election results.
For example, in 2010, the Washington D.C. Board of Elections and Ethics invited a team of experts from University of Michigan (led by Professor Halderman) to try to hack the district’s new online voting system.
Within 48 hours, the University of Michigan team had broken in, taken over the election server, added fictional movie and TV characters as candidates (including for mayor and the member of congress), changed every vote, and revealed almost every secret ballot.
The election officials didn’t realise their system had been hacked for nearly two business days. When they did, it was only because the hacking team left behind a musical “calling card”, changing the Thank You page that appeared at the end of the voting process so that it played the University of Michigan fight song.
A note for NSW voters
We hope there are no more exploitable security problems in iVote and that the rest of the NSW election runs more smoothly.
But since we’ve had no opportunity to inspect the server side code or systems, there’s no way to be sure. When you’re working on the internet, new vulnerabilities emerge all the time.
That’s why, if you want to be sure your vote counts in the NSW election, we recommend you stick with an old-fashioned paper ballot.
An update from the authors
3:20PM UPDATE: Since publishing this article, this issue has been widely covered in by other news outlets, including on ABC radio and online.
The NSW Electoral Commission’s chief information officer Ian Brightwell told the ABC that there was a problem, but it had been fixed and the system was safe.
We are confident however that the system is yielding the outcome that we actually initially set out to yield, and that is that the verification process is not telling us any faults are in the system.
While we are pleased that the NSW Electoral Commission rapidly made changes to iVote in response to our findings, we are concerned that it does not seem to understand the serious implications of this attack.
Before the commission patched the system, the problem could be exploited under realistic and widespread conditions, and the iVote system cannot prove that this did not occur.
The problem was a direct consequence of faulty design in the iVote system, particularly the decision to include code from an external source. Its effect was to allow an attacker to modify votes, which shows the NSW Electoral Commission’s past claim that the vote was “fully encrypted and safeguarded [and] can’t be tampered with” to be false.
We had to demonstrate a breach with the practice system because breaching the actual iVote process carries a penalty of three years in gaol, according to the electoral commission’s website. Since the real system uses identical code, the real system would have been susceptible to the same attack.
The integrity of this NSW election now relies on iVote’s verification and auditing processes – but these provide only limited defence, at best.
The electoral commission’s security testing failed to expose the vulnerability we found, and may have also missed flaws in the server software, verification protocol, and auditing process. The commission has so far declined to make these critical components available for public scrutiny.
* You can listen to the ABC World Today program’s coverage of this issue on March 23, which includes the NSW Electoral Commission response. Or read more of The Conversation’s coverage of the 2015 NSW election.